In a recent report, cybersecurity firm Kaspersky has revealed the discovery of a sophisticated new malware strain named TCESB, previously unseen in the operations of the notorious ToddyCat group. This stealthy tool is designed to silently execute malicious payloads while bypassing traditional system defenses.
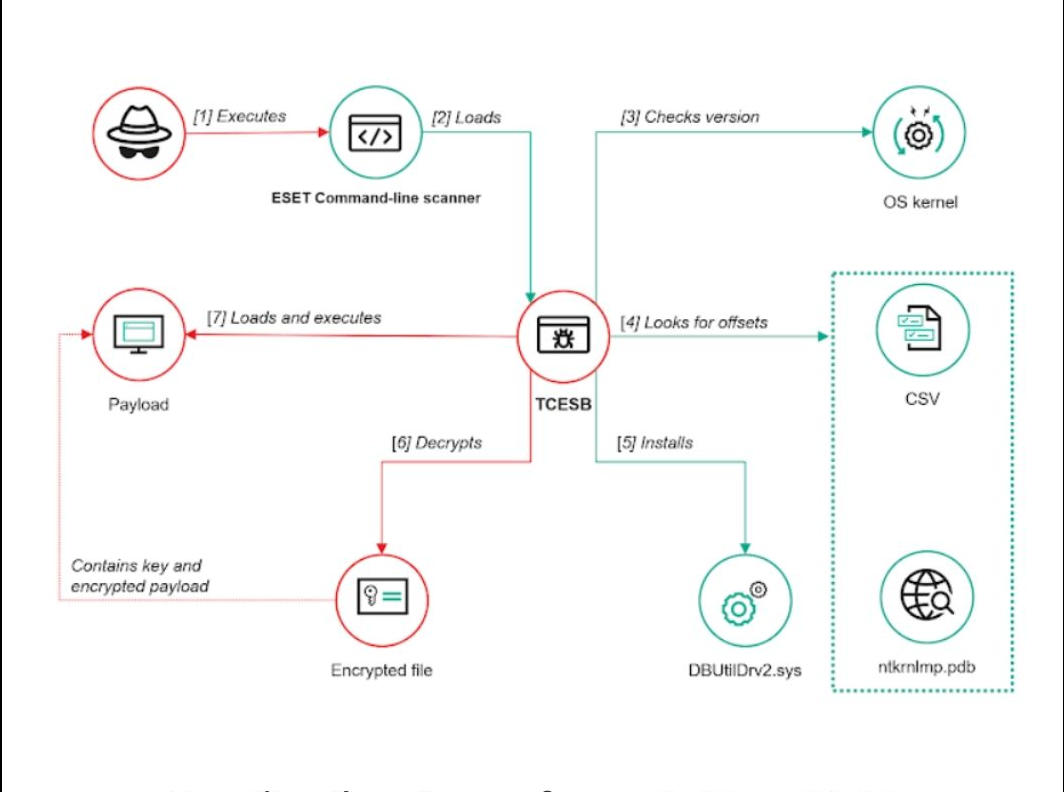
Kaspersky’s investigation, which focused on a wave of ToddyCat-related incidents in early 2024, uncovered a suspicious file named “version.dll” located in the temporary folders of multiple infected devices. Researchers identified it as a 64-bit DLL file that functions as the TCESB malware, deployed using a technique known as DLL Search Order Hijacking. This method allows attackers to hijack the system’s execution flow by exploiting how Windows locates DLL files.
The malware exploits a vulnerability tracked as CVE-2024-11859, which was assigned a CVSS severity score of 6.8. The flaw was responsibly disclosed and subsequently patched by ESET in late January 2025.
In response to this threat, Kaspersky is urging organizations and users—especially those using ESET software—to ramp up system monitoring efforts. Specifically, they recommend scrutinizing installation events involving drivers with known vulnerabilities and watching for abnormal behavior, such as the loading of Windows kernel debugging symbols on systems where kernel debugging is not expected.
This discovery serves as yet another stark reminder of the growing sophistication of cyberattacks and the critical need for regular software updates and layered security measures.