A newly discovered attack vector is exploiting Windows Sandbox to deploy malware while bypassing most antivirus solutions.
Windows Sandbox was originally introduced by Microsoft to allow users to safely test suspicious software in an isolated environment. However, a recently uncovered vulnerability still unpatched has turned this protective feature into a potential threat vector.
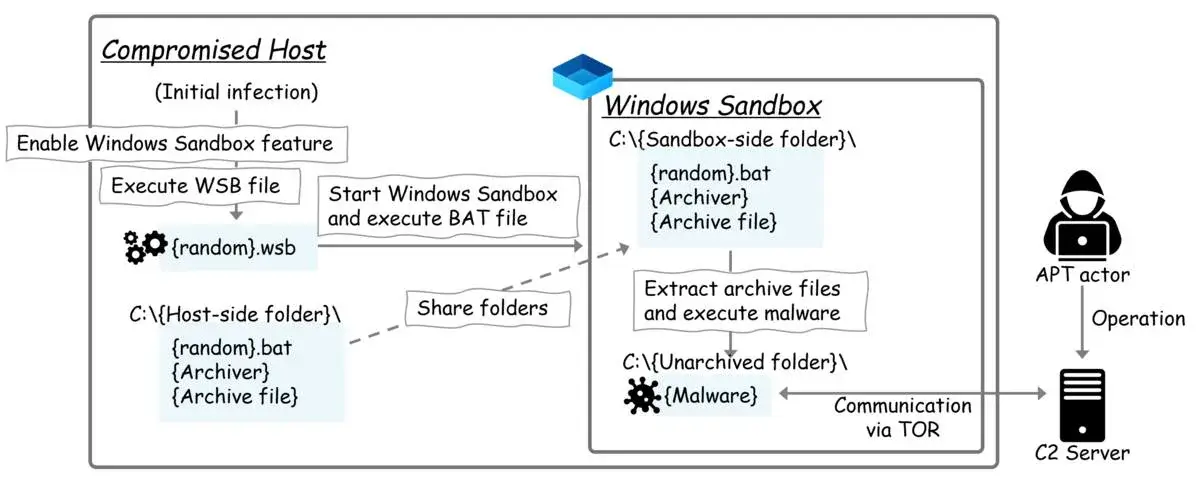
The attack begins when the hacker activates the Windows Sandbox feature and configures a shared folder between the host and the sandbox environment. Once set up, the malicious code is executed within the sandbox. This malware can then exfiltrate stolen data to an external Command-and-Control (C2) server, all while staying invisible to traditional antivirus tools.
The reason this method is particularly dangerous is that antivirus software typically does not monitor or have access to the sandbox environment. This allows the malware to run without being detected, making it an ideal stealth mechanism for attackers.
Security researchers strongly advise users and IT administrators to stay vigilant, disable Windows Sandbox if not in use, and monitor for unusual data transfers or suspicious sandbox activities. Until Microsoft addresses this vulnerability, it represents a serious blind spot in Windows' defense systems.